SCDigest
Editorial Staff
| SCDigest Says: |
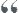 Categorizing potential RFID-based applications as falling into which scenario can help companies understand the likely impact on potential return (lowest to highest) and system software work (also lowest to highest).
Categorizing potential RFID-based applications as falling into which scenario can help companies understand the likely impact on potential return (lowest to highest) and system software work (also lowest to highest).

Click Here to See Reader Feedback |
As RFID has entered the automatic identification mainstream, many companies are looking at how to use the technology in a variety of supply chain operations.
To help think through the application of RFID technology, it may be helpful to think of the potential use of RFID in the context of the predominant supply chain auto ID technology, bar codes. From that perspective, any potential use of RFID may be thought of as occupying one of three categories relative to the current or alternative selection of bar coding for the process/application.
1. Basic Bar Code Replacement: In these scenarios, RFID will operate really just like an “electronic bar code.” Individual bar code scans are simply replaced with an RFID read. There are many examples where this type of application makes perfect sense and can deliver significant benefits. Example applications include pallet identification (e.g., in receiving or shipping), reading cartons on a conveyor system, pallet putaway, reading work-in-process totes, etc.
The advantage of RFID over bar codes in these scenarios usually relate to improved efficiency from eliminating hand scans by operators, or eliminating problems with bar code read rates, as is often found in high speed carton sortation systems.
The “basic bar code replacement” applications are the easiest to implement because the fundamental business process is the same, and the underlying business software application can often remain exactly, not caring (or knowing) whether the source of the identifier was a bar code or RFID tag.
2. Enhanced Business Process: In these cases, the basic business process remains the same, but the unique advantages of RFID begin to be more leveraged. For example, RFID might be used to simultaneously read all of the cartons on a pallet as it passes through a portal, or read all of the serial numbers virtually at once as a pallet of goods leaves a production cell.
In these scenarios, the fundamental process remains the same, but is enhanced to drive even greater productivity. A pallet of bar coded goods cannot be read all at once, and if bar codes on some cartons are not accessible, could not even be read manually after the pallet is built.
(RFID and Automatic Identification Article - Continued Below) |